Azure Client VPN Automated
(Azure says it can’t be done but we did it)
Discover the hidden setting that makes Azure Client VPN Automated work on a Domain Joined Machine
If you are joining us via a search result Bing, Google or another search engine welcome to our website. If you find this information useful and it solves this problem for you that is great. All we ask is that you take a moment to see if any of the services we offer might benefit you. If you would like assistance implementing this solution for you or along with you please contact us today to get our rates and schedule the assistance.
This article will build upon the work of others whose information WSI studied, that helped us come up with this solution. Thank you to the other talented people who have already written on this topic.
Our testing environment consisted of two Microsoft Active Directory Domain Controllers running on Microsoft Azure with 80+ Win 8.1 Pro machines connected to the Domain. These are roaming users with no connectivity to the Domain outside the VPN connection.
Once all was setup we discovered a very strange issue, our clients would do a Group Policy update (GPupdate) for only ten minutes after logon, then the User Policy would apply but not the Computer Policy. If that is acceptable then great, however this was not an acceptable outcome for us! WSI spent countless hours on the phone with different Microsoft Engineers and finally found the fix. Search as you will but this is nowhere to be found on the Web or on TechNet as of the time this article was written. If you need proof try searching for this error: SMBClient/Security Event ID 31001 we had an entry for every time the System made an attempt to update Group Policy. Also saw this one, Event 1058 Account does not exist, if you have other Events something is wrong with your Domain or network setup, ours was pristine as verified by Microsoft Engineers we worked with.
First thing is to setup your Azure Network to support Point-Site Client VPN, also you will want to setup Site-Site capabilities as doing this later may prove difficult. If you never use it that is fine but it is best to have it ready if you need it in the future
http://msdn.microsoft.com/en-us/library/azure/dn133792.aspx
Once you can ping your Azure VM your good to move on
Here is where things fall apart, how do you control the VPN Client Azure gave you to connect to Azure, you do not. It is manual process and there is no way to automate it.
http://feedback.azure.com/forums/217313-networking-dns-traffic-manager-vpn-vnet/suggestions/5282432-auto-connect-for-point-to-site-vpn
Now if we dig deeper we find that we can use c:\rasdial.exe to control a manually created VPN connection. So how do we do that? Before you click the link below, the most important step you will make is to “Allow other Users to use this connection”
You will also find the steps to fix routing via a PowerShell command, this is only needed in Windows 7, Windows 8.1 has this worked out and the PowerShell script is not needed. This has been tested in Windows 7 and works when the PowerShell script is used to fix routing to your new 10.x.x.x Azure VPN connection.
http://www.diaryofaninja.com/blog/2013/11/27/deconstructing-the-azure-point-to-site-vpn-for-command-line-usage
Excellent work done by “Diary of a Ninja” hats off to you!
Once you complete these steps you should be able to run the Rasdial.exe commands to control the Azure VPN connection
Ours was named “VPN-Connection”
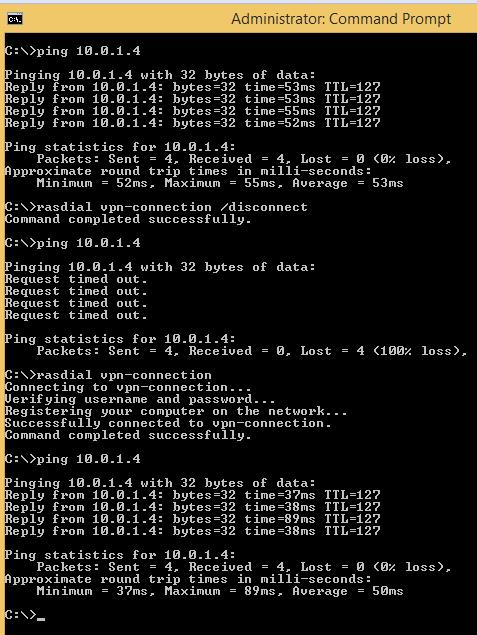
On to the automation side of this, there are a few moving parts.
Things to note, the VPN Client Certificate can NOT be installed as the Computer Account and expect to work for Client logons with Windows 8.1, Windows 7 yes. This means your Windows 8 Client will have to manually install the Certificate and they will need the Private Key, not ideal at all. Here is how we got around that.
PowerShell – file c:\location of PS script.ps1 (best you place this somewhere in c:\windows folder and also set to be hidden)
Script.ps1
$mypwd = ConvertTo-SecureString -String "Certificate Private Key" -Force –AsPlainText
Import-PfxCertificate –FilePath C:\location of\Azurecertificate.pfx Cert:\CurrentUser\My -Password $mypwd
Import-PfxCertificate –FilePath C:\location of\Azurecertificate.pfx Cert:\CurrentUser\Trust -Password $mypwd
Fixes that issue!
Next we need to automate this at logon, here is a scheduled task that will do this for you at client logon, copy to XML File and import into Task Scheduler as Administrator
More information can be found here, we run this task as the System Account
https://technet.microsoft.com/en-us/library/cc725745.aspx
Logon Script we used:
Azure.cmd
if exist %appdata%\cert goto ConnectVPN
powershell -file c:\location of \script.ps1
cd %appdata%
mkdir cert
:ConnectVPN
rasdial vpn-connection
exit
Remember the Certificate thing mentioned above? We create a folder once the Certificate is installed in the Users Profile, and if found, logon script skips past that step.
Ok all is good and you are connected to Azure at logon, all works and you can talk with all VMs created and assigned to your Virtual Network. But what if you are managing a Domain and want to push Group Policies down to Computers and Users?
You will need to modify this file, this is for Windows 8, not yet tested if needed on Windows 7
If you saw above and remember that most important step: “Allow other Users to use this connection”
You will find your Phonebook File here: “Hidden Folder” c:\programdata\microsoft\network\connections\pbk\rasphone.pbk
Open in notepad and modify this line:
UseRasCredentials=1 change this to 0
Reboot and all is well, GPupdate/ force is reliable for both Computer and User Group Policies
We hope you found this information useful and were able to solve this problem. WSI provides full service Microsoft Server and Microsoft Active directory support and configuration services. Please contact us to find out our current rates and schedule a time for one of Microsoft Server/Azure experts to assist you. Winning Solutions, Inc. offers a wide variety of programming and hosting services including design and implementation of your system on Azure or other hosts. Please contact us today for a no charge initial consultation to determine if the services we offer will help you.
Contact us today to get started on moving from an Access Backend Database to operating with a Microsoft SQL Server Database!